 Pointless trivia: This image, nicely depicting the concept of two-factor authentication, was taken from the Hong Kong central bank’s website>
Pointless trivia: This image, nicely depicting the concept of two-factor authentication, was taken from the Hong Kong central bank’s website>
What is Two-Factor Authentication?
Normally, when you log onto a computer-based service, you enter a username to tell the system who you are, and a password to authenticate (prove that you are who you say you are) with the system.
That is one-factor authentication: you are providing only one thing to prove your identity.
Two-factor authentication is a setup where you have to provide more than one thing to authenticate yourself. In most cases, this means your password in addition with some physical device, a hardware-based token. (It is possible to create authentication systems that require even more than two factors. Systems that require two or more factors are more generally called multi-factor authentication).
The YubiKey is an inexpensive ($25) device that provides this sort of additional authentication factor.

How does it work?
The YubiKey is a simple device that plugs into any USB port on your computer. The device has a single button, which, when you press it, spits out a One Time Password (OTP). In the eyes of the computer, the YubiKey is literally just a USB keyboard, and when you press the button, it enters text as if a person is typing (very fast) on that keyboard. Most operating systems support USB keyboards without any additional software, which means that at least on Windows, Mac OS X, and Linux, you can stick the YubiKey into the computer and press the button without having to install any additional software. Needless to say, this makes it incredibly convenient.
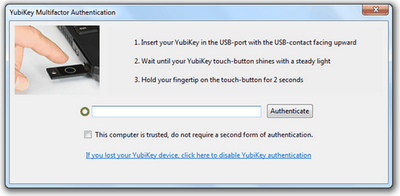
So, when you log into a service that supports YubiKey authentication, you’ll enter your username and password as usual, but you’ll also be presented with a text box for the YubiKey itself to “type” into. You’ll click in the text box as if you’re going to type in it yourself, but instead, you’ll press the YubiKey’s button and it will “type in” a very long password. Then you’ll click to log in like normal, and assuming both your password and YubiKey are valid, you’ll log in.
What makes this more secure?

The idea behind a one-time password is that, as the name states, the password can only be used once. Even if someone is sniffing your network traffic and grabs a copy of the OTP you just used, he can’t turn around and re-use the password itself, as it’s been used and is no longer valid.
The idea being multi-factor authentication is that anyone who wishes to login to services as you has to be able to provide all factors. Stealing your password or stealing your YubiKey isn’t enough - they’d need to have both. That requirement of getting ahold of something that’s physically in your possession dramatically reduces the number of people with opportunity to take your digital identity. A hacker in Russia might be able to set up a website to trick me into giving up my password, but it’s a long flight for him to come get my YubiKey too.
How do I make services “use” my YubiKey?

First of all, to use the YubiKey, the service itself has to support YubiKey authentication. This won’t be common with your average website, but it will be more common with more security-minded services, like LastPass or PassPack.
Secondly, before you can use your YubiKey to authenticate with a service, you have to associate your YubiKey with your account on that service. How this is done depends entirely on how that service has that feature set up. Here, for example, is LastPass’s instruction page for associating YubiKeys with your account on their service.
What about services that don’t support YubiKey?
If a service doesn’t support the YubiKey directly, but does support OpenID authentication, you can use your YubiKey for two-factor authentication by using an OpenID service which supports the YubiKey itself.
Clavid.com is such a service. With a properly set-up Clavid.com OpenID identity, you can have two-factor authentication for any service that does OpenID.
However, outside of those options, there’s nothing you can do to add YubiKey support to a service that doesn’t have it, besides emailing them and bugging them to add it.
What if those services get hacked? Is my YubiKey compromised?
When you register your YubiKey with a service like LastPass, that service does not have your Yubico encrypted identity. All they store is the 12-character Yubico ID. When you tap your YubiKey’s button and send a One-Time Password to that service, they don’t have the means of processing the password and verifying your identity. Instead, they send that password (which contains your 12-character ID) to the Yubico servers, which responds back with a “yes” or “no” to that service. Yubico acts as an authentication gateway for that factor.
So, only Yubico has the information necessary to process the passwords that your YubiKey creates. So, that leads to the question: what if Yubico is hacked? That is the scenario where your YubiKey’s identity may be compromised. Indeed, this happened with another token authentication system recently, RSA’s SecurID. However, as long as you are using YubiKeys for multi-factor authentication, and not as a replacement for passwords, then the result of this would be that your accounts are still protected by your passwords. In other words, you’d be in the exact same place as if you weren’t using YubiKeys to begin with.
The YubiKey website says this thing supports a bunch of different authentication systems. What’s the story there?
The YubiKey is quite a flexible little device, and can indeed be used with a number of different authentication systems.
The most common of these, the thing that people are generally referring to when talking about YubiKey authentication, is Yubico’s YubiKey OTP authentication service. This is what standard YubiKeys come ready to work with right out-of-the-box, and this is what services like LastPass are referring to when stating that they support YubiKey.
However, you can program YubiKeys to support different systems. One thing you can do is program the YubiKey to store a single static password. You press the button, and the YubiKey types in this password. This is a way to be able to create a and use a long, complex password that you can’t possibly memorize. And because it’s just a plain password, you can use it with any password-based system. This isn’t multi-factor authentication (since you’re back to using just a password, not something in addition to a password), but it can be very useful in certain circumstances. Yubico mentions an ideal use case: long passwords for encrypting TrueCrypt vaults.

YubiKeys can be programmed to work with Open Authentication (OATH). Now, read that closely. That is OATH, a system developed by VeriSign, and not OAuth, a system developed by Twitter. It took me a while before I noticed this, as I had only ever heard of OAuth before. Here’s a post from a VeriSign blogger describing the difference between these two unfortunately similarly-named projects. OATH is used in (formerly VeriSign’s, now Symantec’s) VIP authentication system, which we’ll talk about later. Yubico does not run any OATH services themselves.
YubiKeys can also be programmed to work with SAML authentication systems. SAML is used by Google Apps' Single Sign On feature, and Yubico provides a SAML server which can be used to set up SAML-based Single Sign On for your Google Apps domain. Here are Yubico’s step by step instructions for doing that.
In general, these other non-Yubico systems are things you would use with a specific purpose in mind, not for generally-available web services.
Can you use all these services on the same YubiKey?
Originally, YubiKeys supported only one “identity”, meaning you had to pick and choose only one of these authentication systems to use your YubiKey with.
Newer YubiKeys support two identities, so you make one YubiKey work with two different authentication systems. Naturally, most users will have a Yubico identity as one of their two. By default, the second identity is blank, so setting a key up to work with another authentication system requires using one of the free personalization software tools to program the second identity. It can be a little tricky if you haven’t done it before, so be patient and find good instructions (I may write some of my own in another post).
The way that you use a YubiKey with two different services is pretty clever. If you press the YubiKey button for 0 to 1.5 seconds, it outputs the results for the programmed identity in the first slot. Hold the button longer - 2.5 to 5 seconds - and it does the output for the second identity instead. There is a “dead zone” gap in the (approximately) 1.5-2.5 second range so that you can’t accidentally end up at the “border” between the two. Any tap at all is sufficient for triggering slot 1, so you’ll tap for slot 1 and hold the button down for slot 2, and you’ll get nothing at all if you try to let go in no man’s land.
What about the Symantec VIP service?
 The “V” still stands for VeriSign
The “V” still stands for VeriSign
Symantec’s VIP service uses OATH. However, there is a catch. While you can create an OATH-compatible identity, end users like us have no way of getting that identity into the VIP service. They do not provide a means of uploading your own created identity, as Yubico does with their service.
As such, Yubico has created the Symantec VIP YubiKey. It’s a normal YubiKey, except with slot 1 pre-programmed with a Symantec VIP identity, which was entered in to the VIP service at the time of manufacturing, per Symantec’s rules, as explained by the YubiKey YouTube user in this YouTube comment reply:
The [Symantec VIP] YubiKey is the same standard YubiKey - it already supported OATH. The problem is loading secrets and Symantec’s rules are that they can only be loaded at the time of manufacture. Hence the need for a new SKU.
So, if you wish to use a YubiKey with the VIP service, you need to buy the “VIP”-specific model. Note that this model does not come pre-programmed with a Yubico identity, but you are of course free to create one on own for slot 2. Also, the VIP credential is hard-coded into slot 1 and can’t be removed, so you only want to get the VIP model if you do intend on using VIP.
And what if you lose it, or it breaks?

One big issue with multi-factor authentication is, what happens if you lose or damage one of the factors?
Many services have a recovery process for this, where you have to jump through hoops to prove that you’re who you claim to be. It’s also possible to order an identical replacement YubiKey that contains the same identity as the one you lost. Again, here you have to jump through hoops to prove your identity.
But there is a better, more forward-thinking way of protecting yourself from losing or damaging YubiKeys - more YubiKeys! Every YubiKey-compatible service I’ve run into so far allows you to associate multiple YubiKeys to your account, allowing you to authenticate using any one of them.
Thus, I own three YubiKeys: … one on my keyring, … one locked up somewhere safe in my house, … and one locked up in my bank safe deposit box.
Should I lose or break the one on my keyring, I have backups available.
It does mean, however, that for every new YubiKey-compatible service I start using, I need to round up all my keys to associate each of them with the new account. But in practice, this is exceedingly rare - I only have a few things I use YubiKeys with, but they’re important things.
“Would you like to know more?”
I’ll be writing some more posts as I go dig deeper into what you can do with the YubiKey. LastPass and OpenID are certainly cool and sufficient for picking up some YubiKeys, but I think the ability to integrate it with your own services is more interesting.
There is a PAM module for YubiKey authentication, allowing it to be used with things like SSH and VPN. There are also plugins for web-based CMSs like Wordpress. I’m going to dig around and I’ll share what I find.
If you have any questions, please ask them and I’ll try to answer them, maybe in my next post. Also, if anything in this post is incorrect, please let me know and I will correct it. I am simply a consumer and do not work for Yubico or have any stake in their product other than the ~$75 I’ve invested in the three keys I own.
